In an increasingly complex and uncertain business landscape, effective risk management has become a fundamental part of organizational strategy. The ability to identify, assess, and mitigate risks can significantly influence a company’s long-term success, regardless of its size or industry. Whether it’s navigating regulatory changes, financial uncertainties, cybersecurity threats, or operational disruptions, managing risks systematically is crucial.
Compliance Risk and Governance in Delhi is more than just a process of reacting to potential threats. It involves a proactive approach that seeks to anticipate, understand, and prepare for risks before they escalate into significant problems. In this article, we will explore the five key steps in the risk management process and their relevance in safeguarding your business.
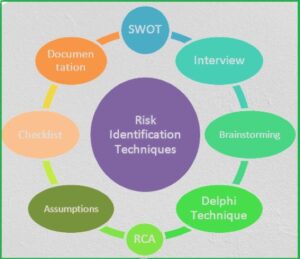
Step 1: Risk Identification
The foundation of any risk management process is the identification of risks. This involves recognizing both the obvious and the less apparent threats that could potentially affect your organization. In this step, it is essential to consider risks that are both internal and external. Internal risks might arise from operational inefficiencies, resource constraints, or poor management decisions. On the other hand, external risks could stem from market fluctuations, regulatory changes, technological advancements, or geopolitical events.
Identifying risks requires a holistic understanding of the business, industry trends, and external influences. To achieve this, organizations typically employ several methods:
Stakeholder interviews and consultations: Speaking to people within the organization, including department heads, employees, and external stakeholders, can provide valuable insights into areas of vulnerability.
SWOT analysis: Evaluating the organization’s Strengths, Weaknesses, Opportunities, and Threats is a standard method for understanding potential risks.
Reviewing historical data: Analyzing past performance and incidents can help identify recurring risks or patterns that could pose future threats.
Industry benchmarking: Looking at competitors and industry standards can highlight risks that are relevant to your particular business context.
Scenario planning: Envisioning various future scenarios allows companies to consider different types of risks and how they may evolve.
Once risks are identified, it is important to document them thoroughly. Each risk should be clearly described, including the source, potential consequences, and the conditions under which it may arise. This documentation forms the basis for the next steps in the risk management process, ensuring that no potential threat is overlooked.
Step 2: Risk Assessment

After identifying potential risks, the next step is to assess their likelihood and potential impact on the organization. Risk assessment allows businesses to prioritize which risks need immediate attention and resources, versus those that can be monitored or tolerated with minimal intervention.
Risk assessment typically involves two key components:
Probability: How likely is it that the identified risk will materialize? Probability can be determined using both qualitative and quantitative methods. For instance, historical data or expert judgment can be used to estimate the likelihood of a risk occurring.
Impact: If the risk were to occur, what would be the extent of its impact on the organization? The impact could be measured in financial terms, operational disruptions, reputational damage, legal consequences, or other significant factors. High-impact risks typically warrant more attention, even if their probability is low.
Risk assessments are often represented visually through risk matrices, where each risk is plotted based on its likelihood and impact. This makes it easier for decision-makers to compare risks and determine which ones need immediate action.
In some cases, more advanced methods like risk quantification may be necessary. This involves assigning specific financial values to risks, allowing businesses to measure potential losses more accurately. Methods like Monte Carlo simulations or decision tree analysis can provide a deeper understanding of risk exposure.
In essence, risk assessment helps create a roadmap for addressing risks. It ensures that resources are allocated efficiently, focusing on the most pressing and dangerous risks first. Without a proper risk assessment, organizations risk spreading themselves too thin, addressing minor issues while ignoring potentially catastrophic threats.
Step 3: Risk Response Planning
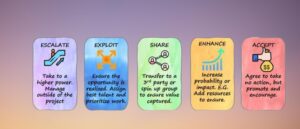
Once the risks have been assessed, the next step in the risk management process is to develop strategies to manage them effectively. Risk response planning involves deciding how to deal with each identified risk based on its probability, impact, and the organization’s risk appetite.
There are four primary strategies for managing risks:
Risk Avoidance: In some cases, it is possible to eliminate the risk entirely by changing plans or processes. For instance, if a particular business venture is deemed too risky, the organization might choose not to pursue it at all. While risk avoidance is the most straightforward approach, it’s not always practical, especially if the risk is inherent to core business operations.
Risk Reduction (Mitigation): Instead of avoiding the risk, organizations may choose to reduce its likelihood or impact. This could involve improving internal controls, upgrading systems, or enhancing employee training. For example, a company concerned about cybersecurity risks might invest in better encryption technologies or conduct regular security audits. Mitigating risks requires balancing the cost of prevention with the potential loss, ensuring that risk management efforts are cost-effective.
Risk Transfer: In situations where a company cannot effectively mitigate a risk, it may opt to transfer the risk to a third party. This can be done through insurance, outsourcing, or contractual agreements. For example, a business might purchase liability insurance to cover potential legal risks or outsource a high-risk function to a specialist firm with better risk management capabilities.
Risk Acceptance: Finally, in some cases, the best course of action is to accept the risk. This strategy is typically used when the risk is low-probability and low-impact, or when the cost of mitigation exceeds the potential loss. By accepting the risk, the organization acknowledges it but takes no proactive measures to prevent it.
Risk response planning is critical because it enables businesses to take control of their risk environment. Without a well-thought-out plan, organizations may find themselves reacting to risks on an ad-hoc basis, which can lead to suboptimal outcomes.
It’s essential to communicate the risk response strategies clearly to all relevant stakeholders. The entire organization should understand what actions need to be taken, who is responsible for implementing them, and the timelines involved. Additionally, risk response plans should be reviewed periodically to ensure they remain relevant in the face of changing circumstances.
Step 4: Risk Implementation

Risk implementation involves putting the risk response plans into action. At this stage, the strategies developed in the previous step are executed to minimize or eliminate risks. Successful implementation requires coordination, communication, and diligent oversight.
Key activities during the implementation phase include:
Assigning roles and responsibilities: Every risk response plan should clearly outline who is responsible for its execution. For instance, in a large organization, the responsibility for managing financial risks might fall to the CFO, while cybersecurity risks may be handled by the IT department. Ensuring that the right people are accountable is crucial for effective risk management.
Developing risk management policies: Policies and procedures should be put in place to guide the implementation of risk strategies. These policies provide structure and consistency, ensuring that risk management is not left to chance. They also help create a culture of risk awareness throughout the organization.
Conducting training and awareness programs: Employees at all levels should be trained on how to identify and respond to risks. For example, a company concerned about compliance risks may need to conduct regular workshops on new regulations and legal requirements. Awareness programs should be ongoing, as the risk landscape is constantly evolving.
Allocating resources: Adequate resources—both financial and human—should be allocated to the risk management process. For instance, mitigating cybersecurity risks may require significant investments in new technologies and additional personnel. Risk management budgets should reflect the priority and severity of the identified risks.
Risk implementation is an ongoing process, and it requires active monitoring to ensure that the plans are being executed as intended. Regular progress checks should be conducted to assess whether risk response strategies are achieving the desired results. If the implementation is not going as planned, adjustments may be necessary.
Step 5: Risk Monitoring and Review
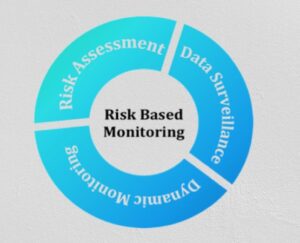
The final step in the risk management process is monitoring and reviewing the risks and the effectiveness of the implemented strategies. Risk management is not a one-time effort. It requires continuous vigilance and adaptation to ensure that the organization remains protected from evolving threats.
Monitoring involves tracking key risk indicators (KRIs) and performance metrics to identify any changes in the risk environment. For instance, if a company has implemented a strategy to mitigate supply chain risks, it should monitor factors like supplier performance, geopolitical changes, or market trends that could affect the supply chain. By keeping an eye on these indicators, the organization can take early action if a new risk emerges.
Regular reviews of the risk management process are also essential. These reviews assess whether the current risk strategies are still effective or if they need to be updated. For example, as technology evolves, new cybersecurity threats may arise, requiring an organization to reassess its digital security protocols. Risk reviews should be conducted at least annually or whenever there is a significant change in the business environment, such as a merger, acquisition, or regulatory shift.
Additionally, feedback from stakeholders should be incorporated into the monitoring process. Employees, customers, and partners can provide valuable insights into potential risks or areas where the current strategies may be falling short. This continuous feedback loop ensures that the risk management process remains dynamic and responsive.
In conclusion, effective risk management requires a structured and proactive approach. By following these five steps—risk identification, risk assessment, risk response planning, risk implementation, and risk monitoring—businesses can protect themselves from potential threats while maintaining operational efficiency and strategic focus. As companies like ACATL, which specialize in corporate legal services, understand, a robust risk management process is essential for long-term sustainability and growth.
FAQs on “5 Steps in the Risk Management Process”
1. What are the five steps in the risk management process?
2. Why is risk identification important in risk management?
Risk identification is crucial as it helps you uncover potential issues before they occur. It provides the foundation for the entire risk management process, ensuring that the organization is aware of what could go wrong and is better prepared to handle it.
3. How does risk analysis differ from risk identification?
Risk identification is the process of discovering potential risks, while risk analysis involves assessing those risks by determining their likelihood of occurring and the potential impact they could have on the organization.
4. What are some common techniques used in risk analysis?
Common risk analysis techniques include qualitative analysis (using expert judgment, risk matrices), quantitative analysis (using statistical models, simulations), and SWOT analysis (assessing strengths, weaknesses, opportunities, and threats).
5. What is risk prioritization, and why is it important?
Risk prioritization involves ranking risks based on their probability of occurrence and the severity of their impact. It’s important because it helps allocate resources efficiently by focusing on the most critical risks that need immediate attention.
6. What are some effective strategies for risk mitigation?
Effective risk mitigation strategies include:
Avoidance: Eliminating the risk altogether.
Reduction: Taking steps to reduce the likelihood or impact of the risk.
Sharing/Transfer: Outsourcing or insuring against the risk.
Acceptance: Acknowledging the risk and preparing to deal with its consequences.
7. How is risk monitoring performed?
Risk monitoring is a continuous process involving regular tracking, reviewing, and reporting of risks. It ensures that new risks are identified, and existing risk mitigation plans are working effectively, allowing for adjustments if necessary.
8. Can risks change over time?
Yes, risks can evolve due to changing circumstances, new developments, or external factors. That’s why risk monitoring and ongoing reassessment are crucial parts of the risk management process.
9. What tools or software can help with risk management?
There are many tools available to assist with risk management, such as:
Risk matrices for assessing risk levels.
GRC (Governance, Risk, and Compliance) software for tracking and managing risks.
Monte Carlo simulations for quantitative risk analysis.
SWOT analysis tools to understand the strengths and weaknesses in risk scenarios.