A risk assessment is a systematic process for identifying, evaluating, and prioritizing risks associated with an activity, process, or organization. It involves:
- Identifying Risks: Determining what could potentially cause harm or problems. This might include hazards, threats, or vulnerabilities.
- Analyzing Risks: Evaluating the likelihood and impact of identified risks. This involves understanding how likely a risk is to occur and the potential consequences if it does.
- Assessing Impact: Gauging the severity of the consequences and the overall effect on the organization or project.
- Prioritizing Risks: Ranking the risks based on their likelihood and impact to focus on the most critical issues first.
- Mitigation Strategies: Developing and implementing strategies to minimize or manage the identified risks. This may involve creating contingency plans, implementing controls, or making changes to reduce the risk.
The goal of a risk assessment is to ensure that an organization can anticipate potential problems and take proactive steps to manage or mitigate them effectively.
Risk Assessment Steps
Risk assessment is a systematic process to identify, evaluate, and manage risks that could potentially impact an organization’s objectives. Here are the key steps involved in a risk assessment:
Identify Risks
Objective: Discover potential risks that could affect the organization.
Methods: Use techniques such as brainstorming, interviews, and historical data analysis. Consider risks from various sources including operational, financial, strategic, and compliance-related aspects.
Analyse Risks
Objective: Determine the nature, cause, and potential impact of identified risks.
Methods: Evaluate the likelihood and consequences of each risk. Use qualitative methods (e.g., risk matrices) or quantitative methods (e.g., statistical models) to assess risk severity and probability.
Evaluate Risks
Objective: Prioritize risks based on their potential impact and likelihood.
Methods: Rank risks to determine which ones pose the greatest threat. Consider risk tolerance levels and the organization’s capacity to manage or mitigate the risks.
Assess Control Measures
Objective: Review existing controls and processes to determine their effectiveness in managing identified risks.
Methods: Evaluate current risk management strategies and controls to see if they are adequate and effective. Identify any gaps or weaknesses in the control environment.
Develop Risk Mitigation Strategies
Objective: Create action plans to manage or mitigate prioritized risks.
Methods: Develop strategies such as risk avoidance, risk reduction, risk sharing, or risk acceptance. Assign responsibilities for implementing these strategies and allocate necessary resources.
Implement Risk Management Strategies
Objective: Put the risk mitigation plans into action.
Methods: Execute the developed strategies and ensure that they are integrated into the organization’s processes. Communicate the plans to relevant stakeholders and provide training as needed.
Monitor and Review
Objective: Continuously track the effectiveness of risk management strategies and make adjustments as needed.
Methods: Regularly review and monitor risk management activities. Conduct periodic risk assessments to ensure that the risk landscape has not changed and that controls remain effective.
Report and Document
Objective: Document the risk assessment process and communicate findings and actions to stakeholders.
Methods: Prepare risk assessment reports that include identified risks, their potential impact, control measures, and action plans. Share these reports with relevant parties such as management and the board of directors.
Continuous Improvement
Objective: Enhance the risk assessment and management process over time.
Methods: Gather feedback, analyze the effectiveness of risk management strategies, and incorporate lessons learned into future risk assessments. Update risk management practices to address emerging risks and changes in the organization’s environment.
These steps help organizations proactively manage risks, ensuring that potential threats are identified, evaluated, and mitigated in a structured and effective manner.
Risk Assessment Techniques
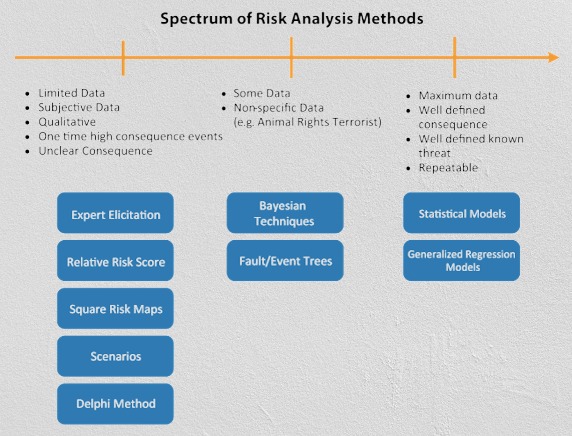
Risk assessment techniques are methods used to identify, analyze, and evaluate risks in order to manage them effectively. Here are some commonly used techniques:
1. Brainstorming
Description: A group technique where team members generate a wide range of ideas and potential risks related to a project or organization.
Use: Identifying risks from various perspectives and encouraging creative thinking.
2. Checklists
Description: A predefined list of potential risks or issues based on past experiences, industry standards, or regulatory requirements.
Use: Ensuring that all possible risks are considered by referencing a comprehensive list.
3. SWOT Analysis
Description: Analyzing an organization’s Strengths, Weaknesses, Opportunities, and Threats to identify internal and external risks.
Use: Understanding risks related to organizational capabilities and external factors.
4. Failure Modes and Effects Analysis (FMEA)
Description: A systematic method for evaluating potential failure modes of a process or system and their effects on outcomes.
Use: Identifying and prioritizing potential failure points and their impact on objectives.
5. Fault Tree Analysis (FTA)
Description: A top-down approach that uses a graphical representation (fault tree) to analyze the causes of system failures.
Use: Determining the root causes of potential failures and their likelihood.
6. Risk Matrix
Description: A tool that uses a grid to assess the probability and impact of identified risks, often categorizing them into levels such as low, medium, or high risk.
Use: Prioritizing risks based on their severity and likelihood.
7. Quantitative Risk Analysis
Description: Using statistical and mathematical models to assess the numerical probability and impact of risks.
Use: Providing a detailed and measurable assessment of risk likelihood and potential impact.
8. Qualitative Risk Analysis
Description: Assessing risks based on subjective judgments and descriptions, often using scales or categories.
Use: Evaluating risks where quantitative data is unavailable or impractical.
9. Scenario Analysis
Description: Evaluating potential future scenarios to understand the impact of different risk events.
Use: Preparing for various possible future events and their impact on the organization.
10. Expert Judgment
Description: Seeking input from experts with specialized knowledge or experience related to the risks being assessed.
Use: Gaining insights and evaluations from individuals with deep expertise.
11. Monte Carlo Simulation
Description: A statistical technique that uses random sampling and computer simulations to estimate risk probabilities and impacts.
Use: Analyzing complex risk scenarios by generating a range of possible outcomes.
12. Delphi Method
Description: A structured technique where experts provide independent opinions through multiple rounds of surveys to reach a consensus on risk assessment.
Use: Achieving a consensus on risk evaluation when dealing with complex or uncertain situations.
13. Bow-Tie Analysis
Description: A visual tool that combines fault tree analysis and event tree analysis to provide a clear picture of risk management and mitigation.
Use: Understanding both the causes and consequences of a risk, as well as control measures to manage it.
14. Risk Registers
Description: A detailed record that documents identified risks, their analysis, and the actions taken to mitigate them.
Use: Tracking and managing risks throughout the project or organizational lifecycle.
15. Sensitivity Analysis
Description: Analyzing how changes in key variables affect the outcome of risk assessments or project performance.
Use: Understanding which variables have the most impact on risk outcomes and decision-making.
These techniques help organizations systematically identify, evaluate, and manage risks to ensure better preparedness and effective Governance Risk Management services in Delhi.
Tools and Software for Risk Assessment

There are numerous tools and software available for risk assessment, each designed to help organizations identify, analyze, and manage risks efficiently. Here’s a detailed list of popular tools and software used for risk assessment:
1. Risk Management Software
RiskWatch: Provides comprehensive risk assessment and management solutions, including risk identification, analysis, and monitoring.
RiskSense: Focuses on cybersecurity risk management and vulnerability assessment, offering insights into risk exposure and mitigation strategies.
Sparta Systems’ TrackWise: A quality management software with risk management capabilities, useful for compliance and regulatory requirements.
2. Project Management Tools with Risk Features
Microsoft Project: Includes risk management features that allow users to identify, track, and mitigate project risks.
Smartsheet: Offers risk management functionalities integrated with project management, including risk tracking and reporting.
Asana: Provides project management features with the ability to identify and manage project risks through task tracking and reporting.
3. Risk Assessment Platforms
Qualys: Provides vulnerability management and risk assessment tools, including continuous monitoring and risk prioritization.
Rapid7: Offers risk assessment solutions with a focus on vulnerability management and threat detection.
LogicManager: Provides a comprehensive risk management platform that includes risk assessment, mitigation, and reporting features.
4. Compliance and Risk Management Tools
RSA Archer: A robust enterprise risk management platform that includes features for risk assessment, mitigation, and compliance.
MetricStream: Provides integrated risk management solutions for assessing, managing, and mitigating enterprise risks.
SAP GRC: Offers governance, risk, and compliance solutions, including risk assessment and management features.
5. Financial Risk Assessment Tools
SAS Risk Management: Offers tools for financial risk assessment, including credit risk, market risk, and operational risk management.
Moody’s Analytics: Provides risk assessment and financial modeling tools for credit risk, market risk, and economic forecasting.
PRMIA Risk Management Software: Offers tools for managing financial risks, including credit, market, and operational risk assessments.
6. Enterprise Risk Management (ERM) Tools
RiskWatch: Provides solutions for enterprise risk management, including risk identification, assessment, and reporting.
Onspring: Offers an ERM platform with customizable risk assessment and management capabilities.
Resolver: Provides an ERM platform with risk assessment, incident management, and reporting features.
7. Cybersecurity Risk Assessment Tools
Nessus: A vulnerability assessment tool that helps identify and prioritize security risks in IT environments.
Qualys Vulnerability Management: Provides continuous vulnerability assessment and risk management for IT systems.
OpenVAS: An open-source vulnerability scanner used for assessing and managing cybersecurity risks.
8. Healthcare Risk Management Tools
RLDatix: Provides risk management solutions tailored to the healthcare industry, including risk assessment and mitigation features.
Quantros: Offers risk management solutions for healthcare organizations, focusing on patient safety and risk assessment.
Patient Safety Net (PSN): A risk management tool designed for healthcare providers to track and manage patient safety incidents.
9. General Risk Assessment Tools
RiskWatch: Provides a range of risk management solutions including risk assessment, mitigation, and reporting.
Enterprise Risk Management Software (ERMS)**: Offers comprehensive risk assessment and management capabilities for various industries.
BWise: A risk management tool that provides risk assessment, compliance management, and reporting features.
10. Visualization and Analysis Tools
Power BI: Microsoft’s business analytics tool that can help visualize and interpret risk assessment data.
QlikView: Provides data visualization and analysis tools for effective risk assessment and management.
These tools and software solutions cater to various needs, from project management and compliance to cybersecurity and financial risk assessment. Selecting the right tool depends on the specific requirements of your organization, including the industry, risk types, and integration needs.
Case Studies and Examples
Here are some illustrative case studies and examples demonstrating how various tools and practices in risk assessment and management have been applied in real-world scenarios:
1. Volkswagen Emissions Scandal

Context: Volkswagen was found using software to cheat on emissions tests, violating Environmental Protection Agency (EPA) regulations.
Risk Assessment: Volkswagen’s internal risk management failed to identify the potential regulatory and reputational risks associated with their emissions cheating.
Outcome: The company faced billions in fines, legal actions, and significant damage to its reputation.
Lesson: Regular compliance audits and robust risk assessment processes could have identified discrepancies in emissions data and prevented the scandal.
2. Equifax Data Breach
Context: Equifax suffered a massive data breach in 2017, exposing sensitive information of 147 million people due to inadequate cybersecurity practices.
Risk Assessment: Equifax’s vulnerability management and risk assessment tools failed to detect and address security weaknesses.
Outcome: The company incurred fines, faced lawsuits, and experienced a significant loss of customer trust.
Lesson: Implementing comprehensive risk assessment tools and regular security audits could have detected vulnerabilities and mitigated the breach.
3. Wells Fargo Fake Accounts Scandal
Context: Wells Fargo employees created millions of unauthorized bank accounts to meet sales targets, violating financial and ethical regulations.
Risk Assessment: The bank’s internal risk management and compliance systems failed to identify and address unethical practices.
Outcome: The bank faced substantial fines, leadership changes, and reputational damage.
Lesson: Enhanced internal and compliance audits could have identified unethical practices early, preventing widespread fraud.
4. BP Oil Spill
Context: The Deepwater Horizon oil spill occurred in 2010 due to inadequate safety measures and non-compliance with environmental regulations.
Risk Assessment: BP’s risk management systems did not adequately address safety and environmental risks associated with offshore drilling.
Outcome: BP incurred billions in fines and cleanup costs, causing significant environmental damage.
Lesson: Regular safety and environmental compliance audits could have identified risks, preventing the disaster.
5. Target Data Breach
Context: Target experienced a major data breach in 2013, affecting millions of credit and debit card accounts due to compromised vendor systems.
Risk Assessment: Target’s risk assessment and vendor management practices were insufficient to prevent the breach.
Outcome: The company faced significant financial losses, legal fees, and reputational harm.
Lesson: Implementing robust cybersecurity risk assessment tools and improving vendor management practices could have mitigated the risk.
6. Sony PlayStation Network Outage
Context: Sony’s PlayStation Network was hacked in 2011, leading to a massive data breach affecting millions of users.
Risk Assessment: Sony’s risk management and cybersecurity measures were inadequate to prevent the breach.
Outcome: The company faced financial losses, customer trust issues, and regulatory scrutiny.
Lesson: Enhancing cybersecurity risk assessment and response strategies could have prevented or minimized the impact of the breach.
7. Toyota’s Unintended Acceleration Recall
Context: Toyota faced a massive recall in 2009-2010 due to unintended acceleration issues in several models.
Risk Assessment: Toyota’s risk management and quality control processes did not adequately address safety risks in vehicle designs.
Outcome: The company incurred significant costs related to recalls and legal settlements, along with damage to its reputation.
Lesson: Implementing more rigorous risk assessment and quality assurance processes could have identified safety issues before they led to widespread recalls.
8. Johnson & Johnson’s Tylenol Recall
Context: In 1982, Johnson & Johnson faced a crisis when cyanide-laced Tylenol capsules led to several deaths.
Risk Assessment: The company’s risk management system responded effectively to the crisis, including a massive recall and new tamper-evident packaging.
Outcome: Johnson & Johnson successfully managed the crisis, restored public trust, and re-established its market position.
Lesson: Proactive risk management and crisis response strategies can effectively handle even severe risks and protect a company’s reputation.
9. American International Group (AIG) Financial Crisis
Context: AIG faced a financial crisis in 2008 due to its exposure to risky mortgage-backed securities and credit default swaps.
Risk Assessment: AIG’s risk management processes failed to adequately assess and mitigate the risks associated with its financial products.
Outcome: The company required a government bailout to avoid collapse, leading to significant financial and reputational damage.
Lesson: Effective risk assessment and management practices are crucial for identifying and mitigating financial risks, especially in complex and high-risk areas.
10. IBM’s Data Privacy Incident
Context: IBM experienced a data privacy incident involving unauthorized access to sensitive customer data.
Risk Assessment: IBM’s risk management and data privacy practices were updated to address the breach and prevent future occurrences.
Outcome: The company implemented enhanced security measures and improved its risk assessment processes.
Lesson: Continuous improvement of risk assessment practices and robust data privacy measures are essential for protecting sensitive information.
These case studies highlight the importance of effective risk assessment and management tools in preventing, identifying, and mitigating risks across various industries.
Risk Assessment Services in Delhi

ACATL is a leading compliance management company based in Delhi, specializing in comprehensive solutions for regulatory compliance and risk management services in Delhi. Their services ensure that businesses adhere to legal requirements while optimizing operational efficiency and minimizing risks.
Types of Risk Assessment Services
Financial Risk Assessment: Evaluates potential financial risks, including credit, market, and liquidity risks, to protect financial stability and compliance.
Operational Risk Assessment: Identifies risks related to business operations, including process inefficiencies, supply chain vulnerabilities, and operational disruptions.
Compliance Risk Assessment: Assesses risks associated with regulatory compliance, ensuring adherence to laws and regulations relevant to the industry.
Cybersecurity Risk Assessment: Evaluates the risks associated with digital assets, data breaches, and cybersecurity threats to protect sensitive information.
Environmental Risk Assessment: Identifies potential environmental risks and impacts related to operations, including waste management, pollution, and regulatory compliance.
Health and Safety Risk Assessment: Focuses on workplace safety and health risks, ensuring compliance with safety regulations and minimizing workplace hazards.
Reputational Risk Assessment: Analyzes risks to the organization’s reputation, including public perception, media exposure, and stakeholder trust.
FAQs on Risk Assessment
Here are some frequently asked questions (FAQs) on risk assessment:
1. What is Risk Assessment?
Answer: Risk assessment is the process of identifying, analyzing, and evaluating potential risks that could affect an organization’s operations, assets, or objectives. It involves assessing the likelihood and impact of these risks to develop strategies for managing or mitigating them.
2. Why is Risk Assessment Important?
Answer: Risk assessment is crucial for safeguarding an organization’s assets, ensuring compliance with regulations, enhancing decision-making, and protecting the organization from potential financial, operational, or reputational harm. It helps in identifying vulnerabilities and implementing measures to prevent or minimize adverse impacts.
3. What are the Key Steps in Risk Assessment?
Answer: The key steps in risk assessment typically include:
Identifying Risks: Determining potential risks that could impact the organization.
Analyzing Risks: Evaluating the nature, likelihood, and impact of identified risks.
Evaluating Risks: Comparing the level of risk against acceptable risk levels and prioritizing them.
Mitigating Risks: Developing and implementing strategies to manage or reduce risks.
Monitoring and Reviewing: Continuously monitoring risks and reviewing the risk management process for effectiveness.
4. What are Common Risk Assessment Techniques?
Answer: Common risk assessment techniques include:
Qualitative Risk Assessment: Using subjective analysis to evaluate risks based on experience and judgment.
Quantitative Risk Assessment: Employing numerical methods and data to measure risks and their potential impacts.
Failure Modes and Effects Analysis (FMEA): Identifying potential failure modes and their consequences.
Fault Tree Analysis (FTA): Analyzing the causes of system failures using a tree-like diagram.
SWOT Analysis: Assessing strengths, weaknesses, opportunities, and threats related to risks.
5. What Tools and Software are Used for Risk Assessment?
Answer: Tools and software for risk assessment include:
Risk Management Software: Applications like RiskWatch, Resolver, and Sparta Systems that help track and manage risks.
Project Management Tools: Platforms like Microsoft Project and Asana that incorporate risk management features.
Spreadsheet Software: Tools like Microsoft Excel for creating risk assessment matrices and models.
Compliance Management Systems: Software that integrates risk assessment with regulatory compliance, such as MetricStream and NAVEX Global.
6. How Often Should Risk Assessments be Conducted?
Answer: The frequency of risk assessments depends on the organization’s needs, industry regulations, and the nature of the risks. Typically, risk assessments should be conducted annually or whenever significant changes occur in the organization’s operations, environment, or regulatory landscape.
7. Who Should Be Involved in Risk Assessment?
Answer: Risk assessment should involve key stakeholders, including:
Management: For strategic insights and decision-making.
Risk Managers: For specialized knowledge and coordination.
Operational Staff: For practical insights into daily risks and issues.
External Experts: For specialized knowledge or an independent perspective.
8. What are the Challenges in Risk Assessment?
Answer: Challenges in risk assessment may include:
Identifying All Potential Risks: Difficulty in foreseeing all possible risks.
Data Availability and Accuracy: Limited or inaccurate data impacting the risk evaluation.
Changing Risk Environment: Evolving risks due to external and internal changes.
Resource Constraints: Limited resources for thorough risk assessment and management.
9. How Can Risk Assessment Improve Decision-Making?
Answer: Risk assessment provides valuable information on potential threats and opportunities, allowing organizations to make informed decisions. By understanding risks, organizations can prioritize actions, allocate resources effectively, and develop strategies to mitigate adverse impacts.
10. What is the Role of Risk Assessment in Compliance?
Answer: Risk assessment plays a crucial role in compliance by helping organizations identify areas of potential non-compliance with regulations and standards. It enables organizations to address compliance gaps, implement necessary controls, and avoid legal or regulatory penalties.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.